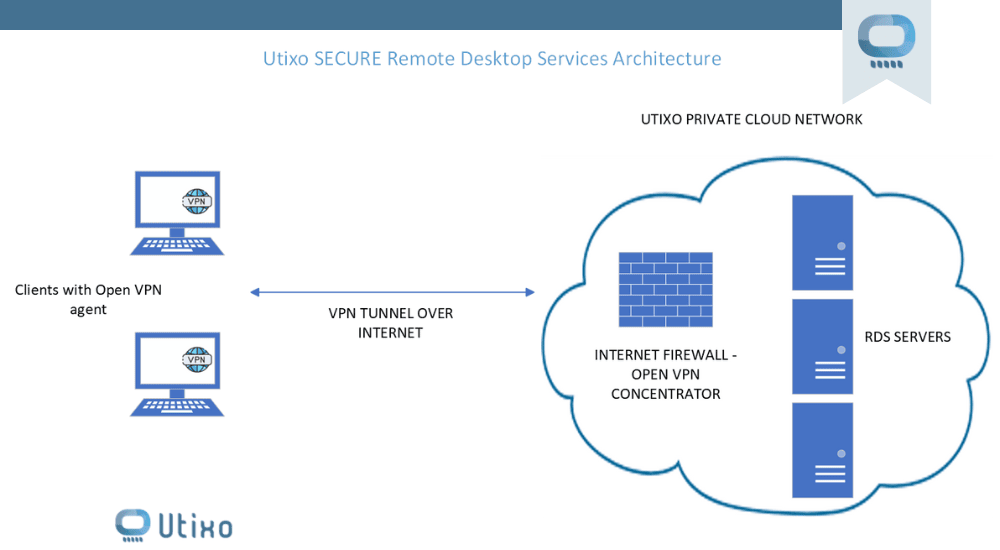
Data retention abroad and GDPR, the latest news

Regulatory updates by Utixo staff attorney and DPO Valentina Apruzzi.
Foreword
With the Schrems II ruling, the European Court of Justice finally swept away the regulatory framework for data transfer and retention abroad. The CJEU enshrined the centrality of the GDPR and pushed the European legislature to focus on the substance of processing. It will also have to define specific measures essential to the transfer of personal data outside the European Economic Area. So, a question arises: is it still possible to transfer data across EU borders legally?
The transfer and storage of data outside the European Union is a very important issue. It is also noticeable based on the significant portion of companies and public administrations that rely on cloud services allocated, at least legally, outside those territories where GDPR applies. The Schrems II ruling today obliges those who “export” information to do so in a reasoned manner. This is because the gap between European and U.S. regulatory scenarios is significant.
This is also an opportunity to learn more about the new standard contract clauses (NCCS) effective June 4, 2021.
Following the Schrems II Judgment and the European Commission's latest measures, is it still possible to lawfully transfer data out of the EU?
The topic is a thorny one, but compared to a year ago when the Schrems II Judgment was issued, there are tools available to be able to make a transfer of personal data outside the EEA. There are cautions to be taken and steps to be taken, but in essence, with a critical and documented approach, transfers can be made. I had a chance to address this issue with some colleagues in the study group of the National Data Protection Association, and we made a report on it.
Following the decision of the Court of Justice of the European Union (“CJEU”) in Case C-311/18 on July 16, 2020, data transfer operations to recipients in countries outside the EEA seemed destined to remain prohibited. For these, an adequacy decision had not yet been adopted by the EU Commission. All because some of the measures in the GDPR to guarantee the transfer were impractical. I am referring, in particular, to the “Privacy Shield” (for transfers to recipients in the U.S.) and the standard contract clauses (“SCC”) approved by the European Commission.
Why would data storage abroad no longer be possible?
The problem stemmed from the fact that the ruling stated that the GDPR’s requirements for adequate safeguards, enforceable rights and effective remedies must be interpreted to mean that data subjects whose personal data are transferred to a third country through the use of SCCs must enjoy a level of protection equivalent to that guaranteed within the EU by the GDPR. This level of protection must take into account both what is contractually stipulated between the European data exporter and the recipient of the transfer established in the third country, as well as those elements of that country’s legal system that conflict with the principles of law applied in the EU and in particular of the Charter of Fundamental Rights of the European Union. The reference to possible access by public authorities in third countries, as found for the U.S., is the track to be followed in interpreting the pronouncement.
Again the CJEU, outlining the strategy for the measures to be taken, ruled that it is up to the data exporter “to make an assessment of the adequacy of the level of protection afforded by third countries to which personal data might be transferred.” In addition, it specified that it is the responsibility of the data controller or processor to “ensure that the lack of data protection in a third country is compensated by adequate safeguards to protect the data subject,” with the possibility of adding other clauses or guarantees.
It is up to the data exporter to analyze whether their transfer outside Europe warrants protection. On the other hand, large U.S. players have simply failed to mention the Privacy Shield in their Privacy Policies. The complexity of the processing and the interests involved make it difficult to imagine that they can, at present, adapt to the vision of the European legislature.
It can be easily understood how much the ruling has wreaked havoc among practitioners, especially among small business entities with reduced budgets to carry out the required investigations and insights. Among the first effects of the ruling, large U.S. players collecting data in the EU simply removed the mention in privacy policies of the Privacy Shield. In addition, they have adopted tout existing SCCs by perjuring themselves not to provide the data to public authorities, but have no means to oppose them.
On the other hand, exporters believed it or pretended to believe it, as long as they could use the services in a state of absolute uncertainty. Of course, this situation did not only affect Italian companies. In some cases, regulators have wasted no time in banning such conduct, as in the case of MailChimp, a marketing service provider.
What are the latest news and changes regarding data retention abroad?
On November 10, the European Data Protection Board (EDPB) published and placed for public consultation “Recommendations 01/2020 on measures that supplement transfer tools to make surecompliance with the EU level of protection of privatedata.” These contain initial guidelines for identifying a method and tools available to make transfers in compliance with the regulations. In addition, the European Commission approved, in a decision dated June 4, 2021, a new set of standard contractual clauses, the new “SCCs,” to be used to guarantee the Article 46 GDPR transfer.
Thus, on the one hand, the EDPB clarified what should be meant by a transfer, what measures would be needed to eliminate or contain the risk of illicit transfers, and on the other hand, the Commission provided an instrument of immediate application.
How can these new tools be used by data "exporters"?
The recommendations and the new SCCs allow a short path to be outlined to support those who would like to transfer personal data out of the EEA safely.
First, it is necessary to start with the census of transfers, direct and indirect, implemented by the manager or sub-manager. What processing entails an extra-EEA data transfer? The board takes this opportunity to clarify that even the mere possibility of access, perhaps for maintenance purposes, to a cloud infrastructure constitutes a transfer and is subject to the ban on extra-EEA transfers. An exception is made when the provider does not offer sufficient contractual guarantees with respect to the fact that the data are not being processed in the Third Country or that the transfer is in compliance with the regulations.
Once the treatments have been identified, where the treatment is not merely occasional, It will then be necessary to verify the existence of an adequacy decision issued by the Commission (the list is public and can be found on the website of the Commission and our Guarantor) With respect to the recipient country of the data. In the case of absence, the appropriate legal instrument must be identified from among those provided by Art. 46 GDPR after assessing its impact by conducting an unplanned assessment (“DTIA” – Data Transfer Impact Assessment). This is where the new SCCs applicable in agreement with the data importer come in. For the adoption of these, however, it will first be necessary to recruit information and assess, on a case-by-case basis, the overall legal framework of the importing country. Not only the regulatory framework is sufficient, but also the associated risk with particular attention to the possibility of access to information by public authorities. As for the adoption of SCCs, the Commission itself explains that standard contract clauses combine general clauses with a modular approach to respond to different transfer scenarios and the complexity of modern processing chains. They come in forms from which the holder is asked to choose based on applicability to his or her own situation and role in the transfer. Their application, however, is not as simple as one might assume because the choice of forms requires rather complex factual and legal assessments.
If the extra-EEA transfer is not based on suitable and sufficient safeguards for “equivalent” protection, additional measures taken will need to be identified and documented. Equivalent protection may come through the adoption of technical measures (e.g., encryption with key reservation in the exporter’s hands, anonymization, pseudonymization, partial processing) and other contractual and organizational measures. To exclude the transfer, therefore, it is not sufficient that the provider-responsible party has its servers within the EEA . In fact, it will also be necessary for it to ensure that it does not access the servers from outside the EEA. If there is no equivalence, all that can be done is to discontinue or not initiate the transfer by ordering the return or deletion of the data to the importer.
The adoption of a formal procedure, to be constantly monitored and updated, is certainly helpful. It makes it possible to avoid making mistakes or forgetting to take relevant aspects into account and to be able to document the process carried out internally.
Can there be an impact on cloud services rendered extra SEE?
Certainly, since a cloud service provider may be located in a non-EEA country and, consequently, the processing would be subject to the regulations and constraints we have discussed. If the importing country is not considered appropriate by the EU Commission, subject to the exceptions provided for in Art. 49 GDPR (occasionality, necessity, consent), it will be imperative to apply one of the adequacy guarantees in the regulations. In addition, if you want to use the new SCCs, you will need to supplement them with additional measures.
For example, Annex II of the EDPB Recommendations, in listing some cases and possible solutions, expressly refers to cloud service providers. In fact, it mentions both the backup service that does not require plaintext data (case 1) and the service that processes plaintext data instead (case 6). The latter stipulates that the transfer can be considered secure only when an encryption system having the following characteristics is in place:
- Personal data before being transferred is encrypted using advanced techniques.
- The encryption algorithm and parameters (including key length) are compliant with respect to the state of the art and can be considered robust in case of decryption attempts performed by public authorities in the importing country.
- The robustness of encryption takes into account the specific period of time during which the confidentiality of encrypted personal data must be preserved.
- The encryption algorithm is flawlessly implemented by properly maintained software whose compliance with the specifications of the chosen algorithm has been verified, such as by certification.
- Keys are reliably managed (generated, administered, stored, if applicable, linked to the identity of an intended recipient, and revoked).
- Keys are kept exclusively under the control of the data exporter or other entities charged with this task. These reside in the EEA or in a third country, understood as a territory or one or more specified areas within a third country deemed appropriate.
As mentioned, of all this there will have to be prior assessment, express agreement with the provider, and procedures and ongoing monitoring with respect to treatment.
Have the Big Tech U.S. (Microsoft, Google, Facebook, Mailchimp, etc.) adapted?
I am not aware of this, but the complexity of the treatments and the interests involved make it difficult to think that they can, at the moment, conform to the vision of the European legislature. Moreover, according to experts in the field, the consequences in terms of loss of users have already manifested themselves.
My advice is to engage experienced consultants to select services that may involve data transfers abroad, conduct the assessments, document them, and keep the processing closely monitored. I believe that the regulations and practice will still undergo many changes, and the penalties are steep.