Lazio Region hacker attack: a lesson not to be forgotten

There are some stimulated reflections of the Lazio Region hacker attack.
From a technical point of view, regardless of the confusion and lack of important details on the issue, we can certainly derive some best practices that Utixo recommends following:
Backup Access: Backup is extremely important and it is critical that it be designed considering the threat of a cyber attack. This, in fact, must be physically separated from the production environment and not directly accessible. Any access to the systems could also encrypt the backup, as would appear to have happened in the case of the Lazio region.
Retention Backup: Unauthorized access to systems may have occurred long before the time when the attack becomes apparent. It means, therefore, that restoring a backup that is too recent may not be decisive; it is necessary to evaluate retention appropriately.
Passwords: The use of simple passwords is now unacceptable, there are dictionaries and software that through brute force techniques can guess passwords and gain access to systems, the use of 2FA and a secure password policy is recommended.
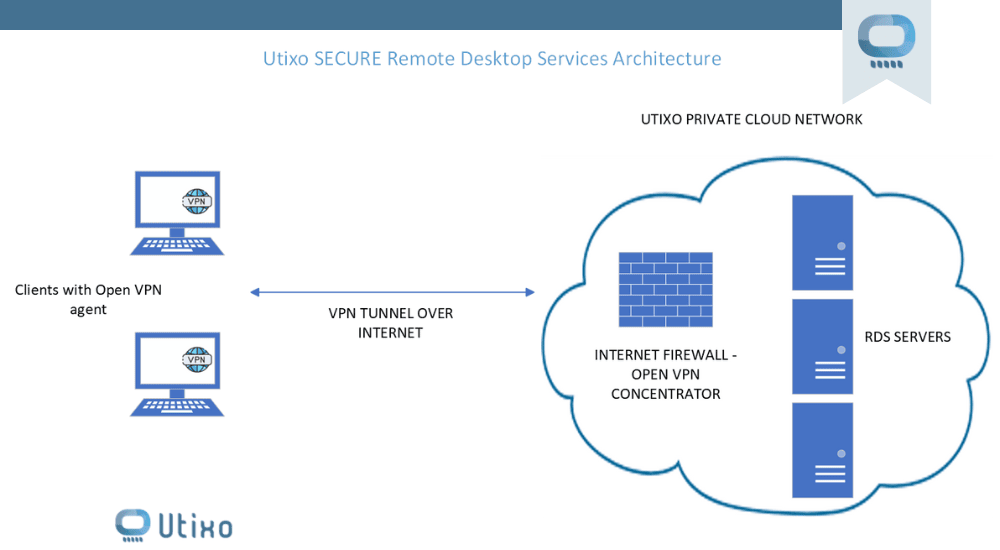
VPN: VPN can no longer be dispensed with. Access to the corporate network and cloud systems should be protected by a VPN that provides proper isolation from the public network. Utixo analysis shows that unprotected VPS servers are “bombarded” with access requests. There is, therefore, a degradation in performance, due to the fact that systems have to handle an overhead to fend off numerous unauthorized access attempts. Utixo recommends activation of the Hybrid Cloud solution that connects the corporate network with the cloud network.
Accounting: Each account must have minimal access to systems in order to perform its roles. If, by chance, even one account is compromised, this should not pose a danger to the entire system. It seems that in Regione Lazio from a single compromised account they got to the main servers.
If you think your network is not secure or have any doubts about it, please contact us as soon as possible! Our network of specialized partners can provide appropriate advice and/or do an audit on your systems (security assessment).